TryHackMe’s DevSecOps Learning Path focuses on securing pipelines and introducing Infrastructure as Code (IaC) and Containerisation security techniques. You’ll learn the tools and practices to ensure robust development processes and secure software deployment workflows. From fortifying pipelines to automating infrastructure management, you will gain practical insights into modern DevSecOps methodologies.
Secure Software Development
Lab: Introduction to DevSecOps
Learning Objectives
- The history behind software development practices and how they’ve evolved over the years
- The importance of this field and the concepts of what makes DevSecOps
- DevSecOps culture and as a discipline
What is DevOps?
DevOps is a set of practices, principles, and tools that combines software development (Dev) and IT operations (Ops) to improve an organization’s ability to deliver applications and services at high velocity. It aims to shorten the software development lifecycle (SDLC) and provide continuous delivery with high software quality.
What methodology relies on self-organising teams that focus on constructive collaboration?
Answer: Agile
What methodology relies on automation and integration to drive cultural change and unite teams?
Answer: Devops
What traditional approach to project management led to mistrust and poor communication between development teams?
Answer: waterfall
What does DevOps emphasize?
Answer: building trust
The infinite loop:
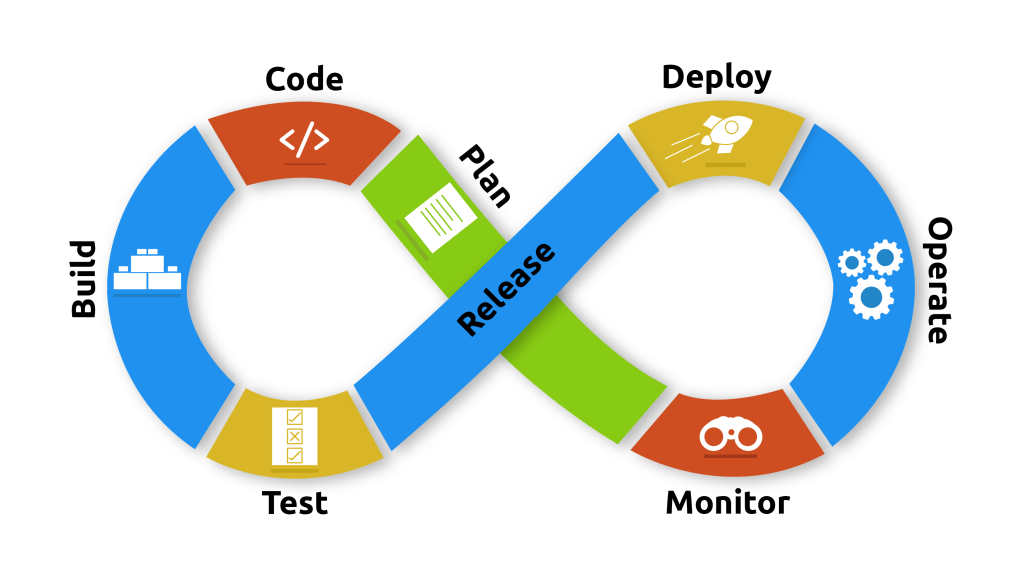
DevOps tools & processes
- CI/ CD – In the previous task, we mentioned CI/CD (Continuous Integration and Continuous Deployment); CI/CD deals with the frequent merging of code and adding testing in an automated manner to perform checks as new code is pushed and merged. We can test code as we push and merge thanks to a new dynamic and routine in deployment, which takes the form of minor code changes systematically and routinely. Thanks to this change in dynamic, CI/CD helps detect bugs early and decreases the effort of maintaining modular code massively, which introduces reliable rollbacks of versions/code.
- INFRASTRUCTURE AS CODE (IaC) – a way to manage and provision infrastructure through code and automation. Thanks to this approach, we can reuse code used to deploy infrastructure (for example, cloud instances), which helps inconsistent resource creation and management. Standard tools for IaC are terraform, vagrant, etc. We will use these tools further in the pathway as we experiment with IaC security.
- CONFIGURATION MANAGEMENT – This is where the state of infrastructure is managed constantly and applying changes efficiently, making it more maintainable. Thanks to this, lots of time is saved, and more visibility into how infrastructure is configured. You can use IaC for configuration management.
- ORCHESTRATION – Orchestration is the automation of workflows. It helps achieve stability; for example, by automating the planning of resources, we can have fast responses whenever there is a problem (e.g., health checks failing); this can be achieved thanks to monitoring.
- MONITORING – focuses on collecting data about the performance and stability of services and infrastructure. This enables faster recovery, helps with cross-team visibility, provides more data to analyze for better root-cause analysis, and also generates an automated response, as mentioned earlier.
- MICROSERVICES – An architecture that breaks an application into many small services. This has several benefits, like flexibility if there is a need to scale, reduced complexity, and more options for choosing technology across microservices. We will look at these in more detail in the DevSecOps pathway.
What helps in adding tests in an automated manner and deals with the frequent merging of small code changes?
Answer: CI/CD
What process focuses on collecting data to analyse the performance and stability of services?
Answer: monitoring
What is a way to provision infrastructure through reusable and consistent pieces of code?
Answer: IaC
Shifting Left
Shifting left means that DevOps teams focus on instilling security from the earliest stages in the development lifecycle and introducing a more collaborative culture between development and security.
Since security can now be introduced early, risks are reduced massively. In the past, you would find out about security flaws and bugs at the very late stages, even in production. Therefore leading to stress, rollbacks, and economic losses. Integrating code analysis tools and automated tests earlier in the process can now identify these security flaws during early development.
This development approach to shifting left in DevOps can be referred to as DevSecOps.
What term is it used to describe accounting for security from the earliest stages in a development lifecycle?
Answer: shift left
What is the development approach where security is introduced from the early stages of a development lifecycle until the final stages?
Answer: devsecops
DevSecOps Challenges
Security Silos
It is common for many security teams to be left out of DevOps processes and portray security as a separate entity, where specialised people can only maintain and lead security practices. This situation creates a silo around security and prevents engineers from understanding the necessity of security or applying security measures from the beginning.
This is not scalable or flexible. Security should be a supportive function to help other teams scale and build security, without security teams being a blocker, but rather a ramp to promote secure solutions and decisions. The best practice is to share these responsibilities across all team members instead of having a specialised security engineer.
Lack of Visibility & Prioritisation
Aim to create a culture where security and other essential application components treat security as a regular aspect of the application. Developers can then focus on development with confidence about security instead of security departments playing police and the blame game. Trust should be built between teams, and security should promote the autonomy of teams by establishing processes that instil security.
Stringent Processes
Every new experiment or piece of software must not go through a complicated process and verification against security compliances before being used by developers. Procedures should be flexible to account for these scenarios, where lower-level tasks should be treated differently, and higher-risk tasks and changes are targeted for these more stringent processes.
What DevSecOps challenge can lead to a siloed culture?
Answer: Security Silos
What DevSecOps challenge can affect not prioritizing the right risks at the right times?
Answer: Lack of visibility
What DevSecOps challenge stems from needlessly overcomplicated security processes?
Answer: Stringent Processes
Exercise: Fuel Trouble
What Software Development Model did the team in Comic 1 follow?
Answer: waterfall
What Software Development Model did the team in Comic 2 follow?
Answer: agile
What Software Development Model did the team in Comic 3 follow?
Answer: devops
What is the flag?
Answer: THM{ONE_TWO_THREE}
Discover more from Information Security Blogs
Subscribe to get the latest posts sent to your email.
