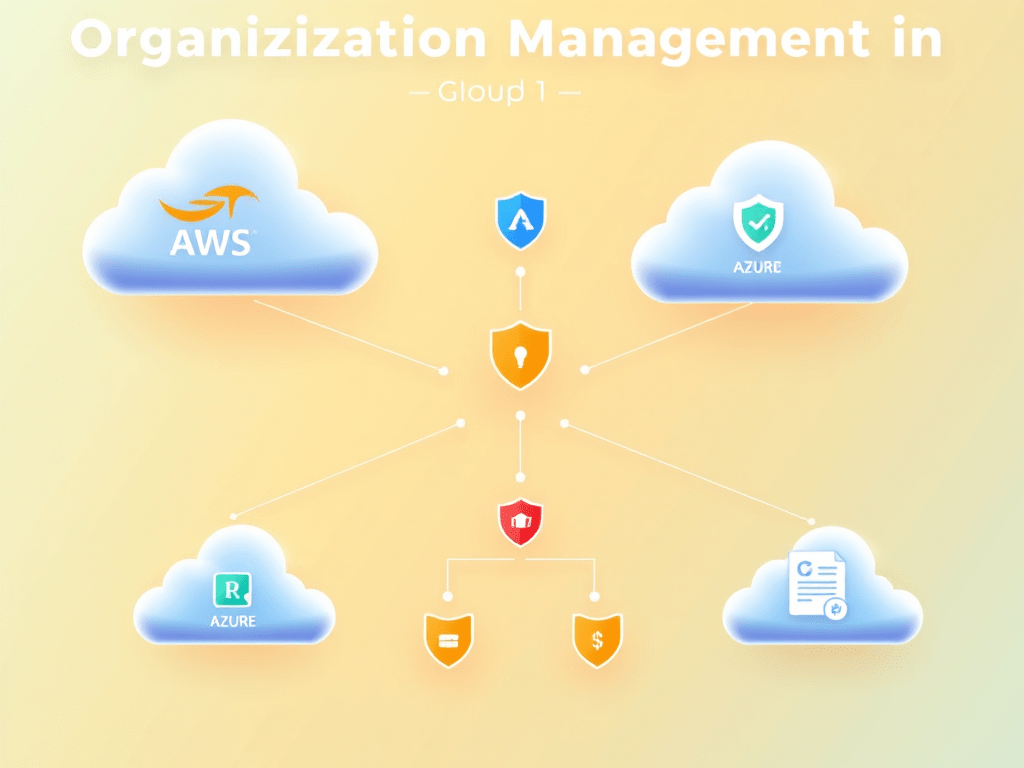
Introduction Organization Hierarchy Models Key Terms: Level AWS Azure GCP Organization Organization Tenant Organization Group Organizational Unit (OU) Management Group Folder Deployment Account Subscription Project Benefits: Segmentation, reduced “blast radius,” logical separation, and compliance alignment. Key Capabilities in Cloud Hierarchy All major CSPs offer: Landing Zone / Account Factory: Building Hierarchies (Three Models) Model DescriptionContinue reading “CCSK Domain 4 Notes: Organization Management”
Tag Archives: informationsecurity
September 2025: Major Data Breaches and Cyber Attacks
Jaguar Land Rover cyberattack deepens, with prolonged production outage, supply chain fallout Jaguar Land Rover (JLR), the U.K.-based automaker owned by Tata Motors, has extended production shutdowns after a cyberattack that disrupted global operations, halted manufacturing, and sent ripples across its supply chain. The company has shut down its IT networks in response to theContinue reading “September 2025: Major Data Breaches and Cyber Attacks”
CCSK Domain 3 Notes: Risk, Audit and Compliance
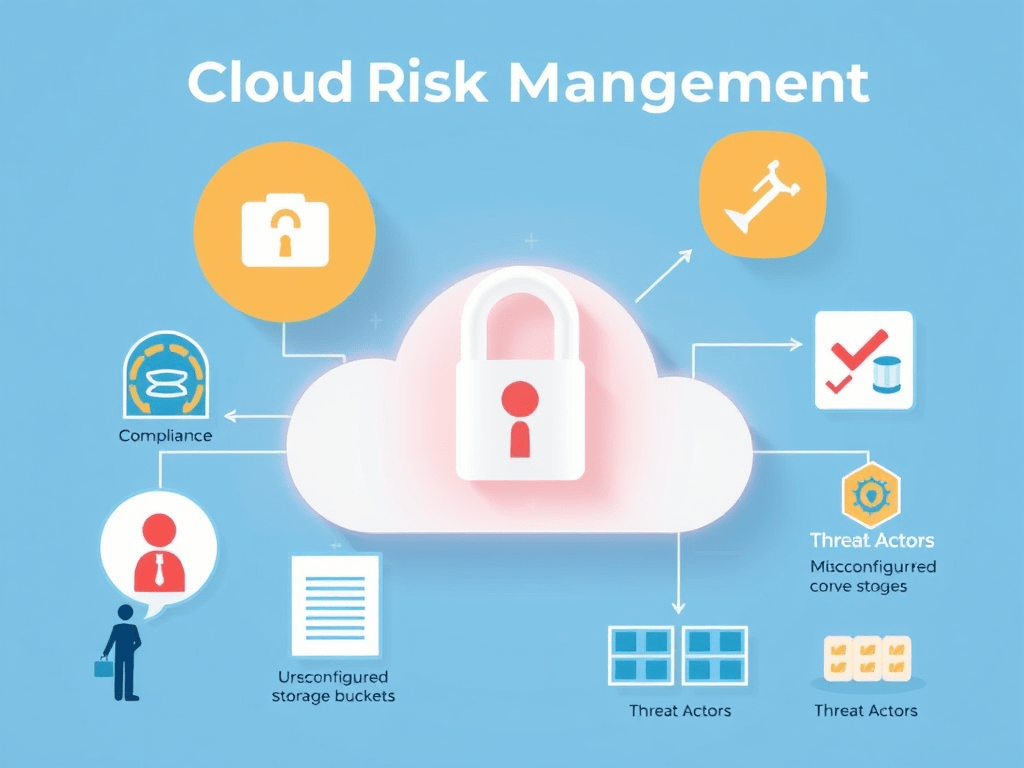
This domain covers evaluating cloud service providers (CSPs) and establishing cloud risk registries, discussing compliance requirements, and introducing tools for governance and risk management. 3.1. Cloud Risk Management Key Concepts in Risk Cloud Risk Factors (Pandemic Eleven, 2022 CSA Top Threats) Common risk factors and categories include: Cloud Risk Management Process (Based on ENISA framework)Continue reading “CCSK Domain 3 Notes: Risk, Audit and Compliance”
August 2025: Major Data Breaches and Cyber Attacks
SABC hacked The South African Broadcasting Corporation (SABC) has confirmed that it was the victim of a business email compromise that affected some of its staff’s email accounts. The state-owned broadcaster’s head of communications, Mmoni Ngubane, told MyBroadband that its IT team has secured the compromised mailboxes. “The SABC is aware of a recent emailContinue reading “August 2025: Major Data Breaches and Cyber Attacks”
CCSK Domain 2 Notes
1. Introduction 2. Cloud Governance Key Points Two major ways cloud impacts governance: 3. Complexities in Cloud Governance 4. Governance Framework Components Effective governance requires: 5. Governance Hierarchy Layers: Governance documents produced: 6. Stakeholder Alignment 7. Cloud Security Frameworks 8. CSA CCM & STAR 9. Policies ✅ Exam Tip: Always tie governance hierarchy → frameworksContinue reading “CCSK Domain 2 Notes”
The Role of NTP Servers in Information Security: Why Accurate Time Matters
In the world of cybersecurity, we often focus on firewalls, intrusion detection systems, encryption algorithms, and endpoint defenses. Yet, one of the most fundamental elements of a secure and reliable IT infrastructure is often overlooked: time synchronization. This is where the Network Time Protocol (NTP) server comes into play. NTP is more than just aContinue reading “The Role of NTP Servers in Information Security: Why Accurate Time Matters”
CCSK Domain 1 Notes
Definitions Essential Characteristics (NIST) Service Models – IaaS → CSC manages OS, apps, data; CSP infra. – PaaS → CSC manages apps; CSP manages platform. – SaaS → CSC manages config only; CSP manages everything else. Deployment Models Core Concepts CSA Enterprise Architecture Shared Responsibility Model Key Tools ✅ Exam Tip: Always link responsibility levelContinue reading “CCSK Domain 1 Notes”
Pretty Good Privacy (PGP)
Understanding Pretty Good Privacy (PGP) and Its Importance in the Digital Age In our increasingly digital world, the security and privacy of communication have become paramount. With the constant threat of cyberattacks, surveillance, and data breaches, individuals and organizations are looking for reliable ways to protect their sensitive information. One of the most well-regarded toolsContinue reading “Pretty Good Privacy (PGP)”
SSL vs TLS: An Information Security Perspective
It is no longer something extra — in the present digital world, security of data is needed more than ever. Many organizations and individuals focus on the security of their online communications, and often the subjects of SSL (Secure Sockets Layer) and TLS (Transport Layer Security) arise. Although SSL and TLS can be mentioned inContinue reading “SSL vs TLS: An Information Security Perspective”
July 2025: Major Data Breaches and Cyber Attacks
Axis Max Life Insurance Announces Data Breach Axis Max Life Insurance, has reported being notified by an anonymous source about their unauthorized access to some customer information in a data breach. The incident has prompted a comprehensive security assessment and rigorous data log analysis. The company released a statement confirming the initiation of a detailedContinue reading “July 2025: Major Data Breaches and Cyber Attacks”